
0x01 Event Background
on May 30, 2023, the EDE Finance project on the Arbitrum chain was subjected to a hacker attack. The attacker profited 597,694 USDC and 86,222 USDT, with the attacker’s address identified as 0x80826e9801420e19a948b8ef477fd20f754932dc. After the attack, the perpetrator left a message on the chain claiming it was a white hat action. Currently, the attacker has returned 333,948 USDC and 86,222 USDT to the EDE Finance project, leaving a portion of USDC untransferred. The Zero Hour Tech security team promptly conducted an analysis of this security incident.

0x02 Attack Steps
Attack Time Background: The attacker had previously set up the attack contract: 0x6dd3d2fb02b0d7da5dd30146305a14190e6fb892
Transaction hash for creating the attack contract: 0xd7bfe2ed548c40d3e9b301a83f16e9c4080e151470ebf4d03c83ff302b9ad99e
An attack contract is a proxy contract, its main logic contract is located at: 0x171c01883460b83144c2098101cd57273b72a054, which has not been contract-verified.
The attacker’s set of attack transactions includes: 0xc3677aec922f3c0641176277d9923bf03ff400e9b79013ba86ac8ceb878fcd86 0x6e48dbe65c9997d774d75bc01468a354c3660a44eef59a4383639933a50fc814
The EDE project’s price Oracle contract VaultPriceFeedV21Fast: 0x046600975bed388d368f843a67e41545e27a2591
The EDE project’s Router contract: 0x2c7077cf9bd07c3bc45b4e5b8c27f8b95c6550b3
The EDE project’s RouterSign contract: 0xd067e4b0144841bc79153874d385671ea4c4e4df,
This contract address has Updater administrator rights, which can be used for setting the price of encrypted assets, as shown in the image below.

Attack steps
The attacker invoked the attack contract, which is indirectly called the add position operation in the RouterSign contract.
Immediately afterward, the attacker used the attack contract to call the reduce position operation in the Router contract.


Subsequently, the attacker repeated the above attack steps, making large profits through multiple additions and reductions of positions.
0x03 Core Vulnerability
Based on the analysis of the attack transactions, it was found that the attacker made a substantial profit by taking advantage of the price difference used directly in adding and reducing positions. The specific analysis process is as follows:
Price used when adding positions:

Price used when reducing positions:
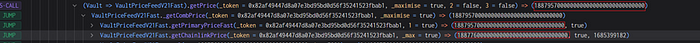
There is a noticeable difference between the prices used for adding and reducing positions.
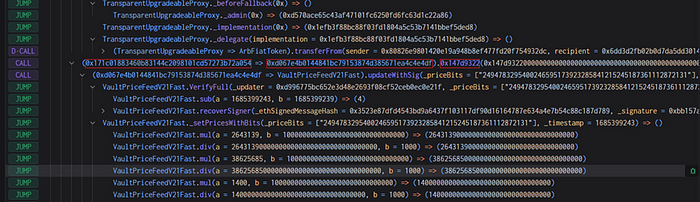
By examining the call stack of the attacker’s transactions, it was found that when adding positions, the attacker called the update price function (updateWithSig) of the price oracle in the EDE project. The price feed function of the oracle not only requires the existence of the Updater privileged role, but also requires that the Updater role is used to sign in order to call it normally.

However, the attacker exploited the add position function of the RouterSign contract, indirectly invoking the privileged function updateWithSig in the price oracle, thereby successfully bypassing the original onlyUpdater permission restriction.

Moreover, due to a problem with the signature verification mechanism in EDE’s price oracle, even though the signing time was checked, no verification was carried out on signatures that have been used, allowing the attacker to replay the administrator’s signature.

The following is the signature parameter passed by the attacker indirectly calling the price feed function of the oracle:
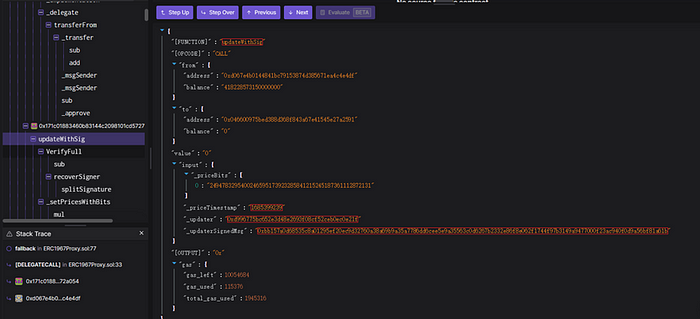
The following is the parameters used by the EDE project administrator directly calling the price feed function through the oracle contract:

So, in summary, the attacker used the administrator’s signature, bypassed the onlyUpdater restriction, successfully replayed and set a higher Token price, and then immediately used the new price to add positions. Subsequently, the attacker immediately called the Router contract to reduce positions using the normal price, thus profiting from the significant price difference.
0x04 Source of Attack Funds
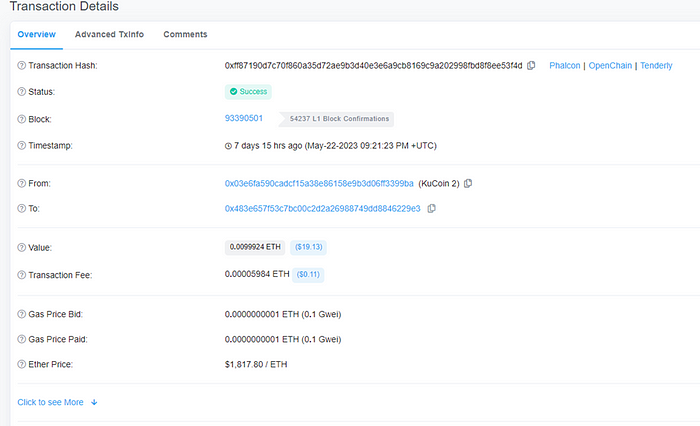
Upon analysis, it was found that the initial transaction fee of the attacker address was transferred in as 0.002ETH from the address 0x483e657f53c7bc00c2d2a26988749dd8846229e3.
The initial transaction fee for the address 0x483e657f53c7bc00c2d2a26988749dd8846229e3 was withdrawn through the Kucoin exchange.
0x05 Summary and Suggestions
Analysis Summary The attack occurred due to a lack of security audits when the project added new contracts. The new contracts broke the original contract’s permission authentication mechanism, and combined with the Updater’s signature replay issue, these two exploitation points were used in combination. Attack exploitation points: • Bypass of Updater’s privilege restriction for updateWithSig in the RouterSign contract • Replay of the Updater’s privileged signature Security Suggestions
- Add unique identifiers to the signature verification of the project’s price oracle feed, and restrict each signature to be used only once.
- The project needs to confirm whether the functional functions in the RouterSign contract can be made public and set permission checks.
